Web Content Blocker Tier List
Jul. 14, 2022 [Technology] [Privacy-Security] [Libre]Many insist that the modern web has become unusable without the aid of powerful content blocking tools. Everybody, technical or otherwise, should install some such addon for their browsers.
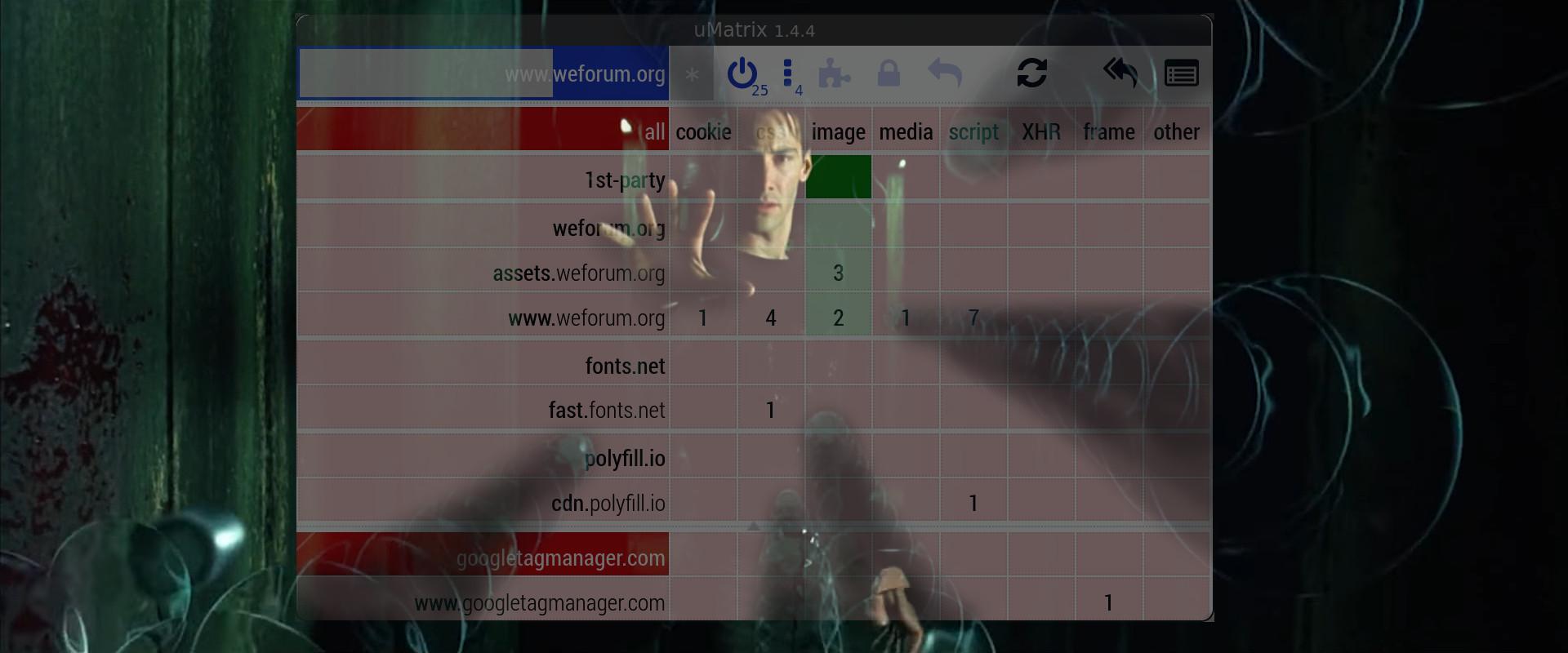
Few are great, most not so much. I rate them here based on their effectiveness in their default-deny capacity to strip pages down to plain HTML, their granularity and how well they convey information about web requests/page elements.
| Tier | Addon | Notes |
|---|---|---|
| S | uMatrix, xiMatrix | Unrivaled web page firewalling. |
| A | Policy Control | Excellent and contains advanced features, but makes unfortunate design concessions. Would handily enter S tier if minor shortcomings addressed. |
| B | uBlock Origin (Advanced User Mode), NoScript Security Suite | Highly granular and informative but unable to completely block certain classes of requests. Interface is suboptimal. |
| C | HTML Content Blocker, Javascript Firewall | Reasonably capable of de-fanging sites but rather limited in scope. |
| D | uBlock Origin (Basic User Mode), Adblocker Ultimate, Adguard AdBlocker | Low capability. Heavily blocklist oriented rather than by class of request. Default deny infeasible. |
| F | Adblock Plus, Privacy Badger, Ghostery, Firefox Enhanced Tracking Protection (Strict) | Garbage tier. Major shortcomings. |
Detailed Rationale
uMatrix:
Despite being in maintenance mode, uMatrix maintains exceptional effectiveness against a wide class of web requests. It is basically a full browser firewall which can discriminate requests globally or per-domain/subdomain and each request class can be blocked individually from one another. Unfortunately, if uMatrix ever falls out of viability, we would lose an almost irreplaceable line of defense.
Policy Control:
Policy Control is one gem that left me impressed. It can block many request types including WebSockets, Ping and Fonts. There is an included logger to monitor requests and can whitelist per script within the same domain, making Policy Control unique among extensions in its granularity. Just make sure to check “enabled” for rules to apply globally. This isn’t made quite clear as that field normally says “disabled” and flips when you toggle it. Unfortunately, it automatically opens add0n.com (cuckflared + googleslavemanager) after installation. Some marks against it being that there’s currently no way to distinguish between third party domains and no interception is offered for cookies. Somehow only known about and used by only 791 people at the time of this writing.
uBlock Origin (Advanced User Mode):
Demoted to B tier.
Not as capable as uMatrix in whole-site default deny, and fails miserably when tasked with any finer granularity such as blocking javascript from one third party domain exclusively. Its inadequate toggle grid poorly conveys information about web requests. uBlock Origin is supposedly capable of higher precision by manually writing noop rules in textual custom rulesets but this is a completely impractical and unrealistic way to try and compete with uMatrix’s brilliant switchboard grid. There are unique capabilities it has such as cname uncloaking and the element zapper. Recently, I found that once an asset has been allowed to load, subsequently blocking it again fails to block that asset… what’s going on uBlock Origin? Is this a regression?
(Basic User Mode):
Demoted to D tier.
Aside from doing some clever tricks under the hood (that make it a great second-line of defense behind real blockers), uBlock Origin in basic user mode is only made noteworthy by it’s element picker, fonts blocking and infamously extensive blocklists. Otherwise, it’s not actually all that much better than Adguard Adblocker or Adblocker Ultimate.
There should be no styling or images after having reloaded that page...
xiMatrix:
One of the few holistic, grid-based addons. It can block by request type, domain and subdomain while global scope very wisely adheres to default deny behavior. It can also handle remote fonts. Rules are written neatly in XML, making for easy textual rule making as well. xiMatrix has recently added a column for cookie blocking, completing the grid of common tracking requests. However, it does not distinguish between image and video content (which compelled me to extend it into paraMatrix). xiMatrix has really begun to realize its potential. S-tier status achieved.
NoScript Security Suite:
Capable of discriminating globally and per-domain/subdomain. It is also capable of blocking elements not individually covered by uMatrix such as webgl. Unfortunately, it doesn’t seem to be able to strip all requests from a domain as it maintains rather permissive css rules. NoScript also defaults to very permissive site templates (probably for normies) which need to be removed or overridden before global default deny can be enabled. Custom rules default to “ANY SITE” scope. I also want to mention a long time has passed since the author was found whitelisting ads. I think he has turned around and become a force for good among addon development, contributing the NSCL and also being one of the developers behind the respectable JShelter.
Javascript Firewall:
Definitely took inspiration for its toggle grid. Actually quite robust with similar layout options. Just that it only has js, xhr and frames in scope. There is a global scope setting (wildcard in dropdown) which rightfully defaults to deny. The toggle grid controls are more like an old cellphone keypad with clicks cycling through default(light green/red) / allow(dark green) / block(dark red). Javascript Firewall just doesn’t go far enough. It could relatively easily be expanded into a more powerful tool. Somehow only has 17 users at the time of this writing.
HTML Content Blocker:
I was pleasantly surprised at the simplicity of HTML Content Blocker relative to how effective can be. It is hampered by being only global in scope and only capable of dealing with just five request types; js, css, img, obj, media. The default is to allow all categories so toggle each category off before loading any pages (to set global deny). HTML Content Blocker is fast and dead simple.
Adblocker Ultimate:
Very blocklist oriented but at least has an element picker. Default allow with no possibility to default deny. Low tier.
Adguard AdBlocker:
One redeeming quality of Adguard is its dedicated logger window which shows requests by category and can be filtered by all, tab, etc. It may be possible, albiet clunky, to write custom rules based off logger information. Filters are automatically downloaded on first run. Otherwise it’s like Adblocker Ultimate.
Adblock Plus:
Adblock Plus is still up to their old antics with whitelisting “acceptable” partner ads, which has now been made opt-out. Can be configured in the global settings to block social icons, cookies and push notifications. Barely helpful for anyone who knows how to configure their browser.
Privacy Badger:
Can block by domain, but idiotically forces users to wait until the third party domain has been recognized on other sites or for the user to manually block after the damage has already been done. “The domain does not appear to be tracking you: \www.googletagservices.com” lol. Even though it is possible to block things manually (and clumsily), I think this addon is just meant to be a set-and-forget helper for grandmas.
Ghostery:
Advertises a “block by default” option but still fails massively by letting various resources through. You can restrict things on a per-site basis and Ghostery does a moderate job at informing what has been blocked vs allowed in the detail view. But new domains cannot be manually blocked until after they have been encountered in the wild. Has a setting “A/B tests” which is opt-out data collection. Oh man, it gets worse. Ghostery now also requires users to agree to terms and conditions before enabling blocking functionality. I would never expect anyone to rely on Ghostery.
Firefox Enhanced Tracking Protection (Stict settings, built-in):
Per-site toggle and enabled by default. Although it is list based with no interactive way of discriminating by web request type. You can only look at the block statistics history. It’s probably supposed to be overly simple but ETP is pretty pathetic on its own as a content blocker.
*Evaluated within a fresh Firefox-ESR base with suggested Arkenfox hardening applied and anonymized DNS routing (at host).
Other Noteworthy Addons
JShelter:
REMOVED FROM LIST
as JShelter falls outside the scope of content blocking. It instead aims to mask/falsify data to javascript. One goal is to generate unique fingerprints, per session and per domain so that fingerprinters cannot build up a persistent identifier. From their FAQ: Does JShelter replace a tracker blocker?
No, many extensions specialize in list-based tracking. We consider list-based tracking out-of-scope of the JShelter mission. You should keep using a tracker blocker like uBlock Origin in parallel with JShelter. We believe that web extensions like NoScript Security Suite and uMatrix origin are good but do not protect the user from accidentally allowing malicious code.
So it is therefore preferable to run JShelter behind an existing whitelist firewall like uMatrix, while allowing JShelter to act as a second-line of defense sanitizer for those scripts that you do allow.
Trace:
REMOVED FROM LIST
because, like JShelter, it is an anti-fingerprinting tool. It could be considered a rather glorified browser settings tweaker with blocklists stuffed in. Trace modifies requests and spoofs information. Some additional marks against it are the site being cuckflared (and, by extension, the blocklist updates) and the code being marked “All Rights Reserved”, despite being posted on a git repository. Just use JShelter instead.